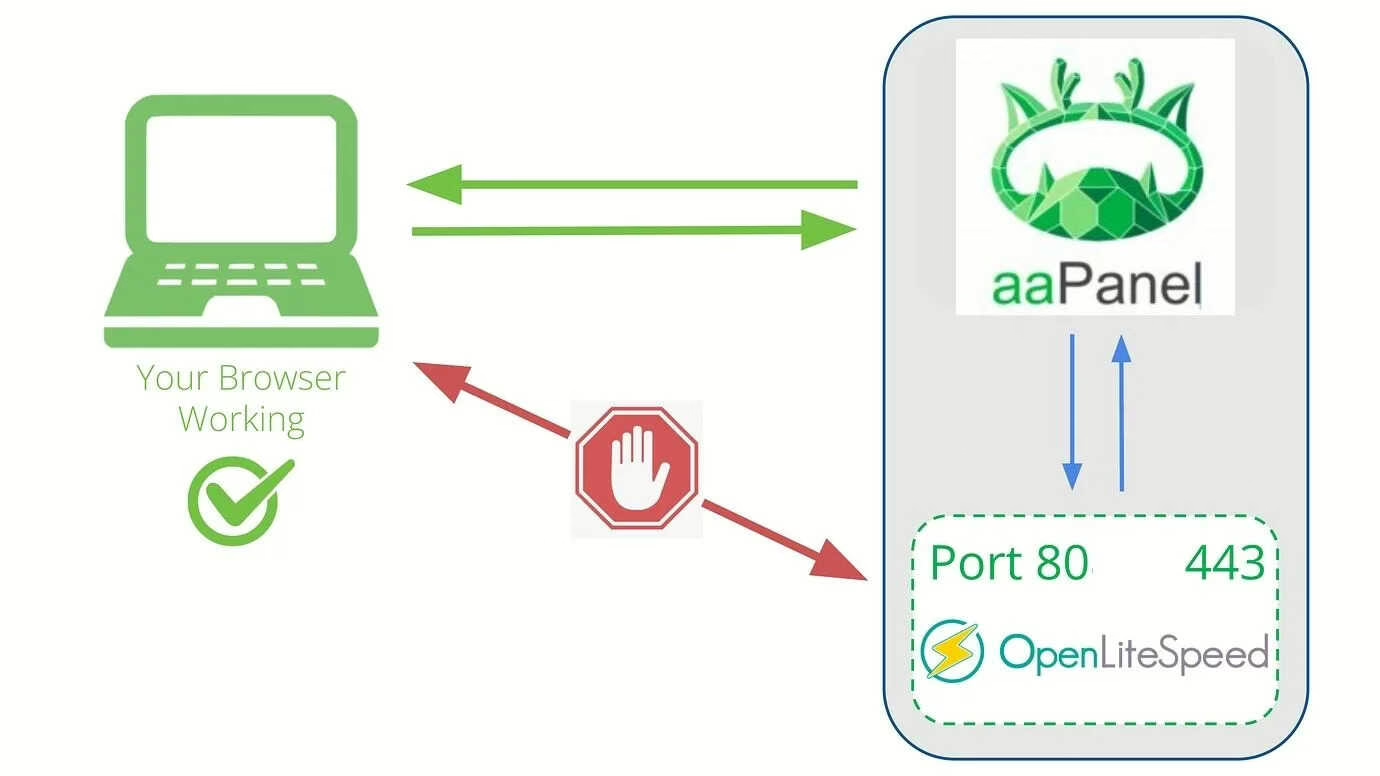
How to configure AntiDDoS Protection on aaPanel with vDDoS Proxy Protection for openlitespeed as backend.
In today’s digital landscape, where cyber threats continue to evolve and pose significant risks to online businesses, ensuring the security and stability of your virtual private server (VPS) is of utmost importance. One such threat that can cripple your server’s performance and disrupt your online presence is a Distributed Denial of Service (DDoS) attack.
To safeguard your VPS against these malicious assaults, it is crucial to implement reliable anti-DDoS protection. In this blog, we will discuss, how to configure AntiDDoS Protection on aaPanel with vDDoS Proxy Protection for openlitespeed as backend, what are the steps you can take to configure vDDoS protection on your vps server running aaPanel, empowering you with the knowledge and tools to defend against DDoS attacks effectively.
Step 1: Install aaPanel on your vps
To begin the process of configuring vDDoS protection on your VPS, the first step is to install aaPanel, a powerful web hosting control panel that simplifies server management tasks. Follow the steps below to install aaPanel on your VPS:
Connect to your VPS: Use a secure shell (SSH) client such as PuTTY (for Windows) or Terminal (for macOS and Linux) to establish a remote connection to your VPS. Ensure that you have the necessary login credentials (username and password) or SSH key.
Update system packages: Before proceeding with the installation, it is recommended to update your system packages to their latest versions. Run the following command to update the packages:
sudo apt update && sudo apt upgrade
For CentOS or other Red Hat-based systems, use the following command:
sudo yum update
Download aaPanel installation script: Once your system is up to date, download the aaPanel installation script using the following command:
wget -O install.sh http://www.aapanel.com/script/install-ubuntu_6.0_en.sh && sudo bash install.sh
This command will retrieve the installation script and execute it using sudo privileges.
Follow the installation prompts: The aaPanel installation script will guide you through the installation process, prompting you for necessary information such as your preferred language and server IP address. Follow the on-screen instructions, and enter the required details when prompted.
Access aaPanel: Once the installation is complete, you can access aaPanel by visiting your server’s IP address in a web browser followed by “:8888”. For example, if your server’s IP address is “123.45.67.89”, you would access aaPanel by entering “http://123.45.67.89:8888” in the browser’s address bar.
Congratulations! You have successfully completed the first step of installing aaPanel on your VPS. In the next steps, we will explore the process of configuring vDDoS protection and strengthening the security of your server.
Step 2: Configure your server with openlitespeed web server
Once you have successfully installed aaPanel on your VPS, the next step is to set up essential components such as OpenLiteSpeed server, phpMyAdmin, and MySQL or MariaDB database using the app store within the aaPanel admin dashboard. Follow these instructions:
Access aaPanel admin dashboard: Open a web browser and navigate to the aaPanel admin panel by entering the URL “http://your_server_ip:8888” (replace “your_server_ip” with the IP address of your VPS). Log in using the credentials you provided during the aaPanel installation.
Navigate to the App Store: Within the aaPanel admin dashboard, locate and click on the “App Store” option. This will take you to the aaPanel App Store, where you can find various applications and services to install on your VPS.
Install openlitespeed server
Search and install OpenLiteSpeed: In the app store’s search bar, type “OpenLiteSpeed” and press Enter. Look for the OpenLiteSpeed package and click on the “Install” button next to it. Follow the on-screen instructions to complete the installation process. OpenLiteSpeed will serve as the web server for your VPS.
Install phpmyadmin
Install phpMyAdmin: After installing OpenLiteSpeed, search for “phpMyAdmin” in the app store’s search bar. Locate the phpMyAdmin package and click on the “Install” button. Follow the prompts to install phpMyAdmin, a popular web-based interface for managing MySQL or MariaDB databases.
Install mysql or mariadb server
Install MySQL or MariaDB: Once phpMyAdmin is installed, search for either “MySQL” or “MariaDB” in the app store’s search bar, depending on your preference. Click on the corresponding “Install” button to install the desired database management system. Follow the installation prompts to complete the setup.
Congratulations! You have successfully set up OpenLiteSpeed server, phpMyAdmin, and MySQL or MariaDB on your VPS using the aaPanel App Store. These components are essential for hosting websites and managing databases, providing a solid foundation for your server’s functionality. In the next steps, we will delve into the configuration of vDDoS protection and further securing your server.
But for configuring vDDoS protection to you server you first have to add atleast one website in your server, just navigate to website menu in your admin dashboard of your aaPanel dashboard and create a website there and put some content on it.
Enhancing the security of your VPS is crucial. In this article, we will explore the process of adding vDDoS protection, a robust defense mechanism against DDoS attacks, to fortify your server’s resilience and ensure uninterrupted online presence.
Step 3: Install vDDoS Proxy Protection
Install vDDoS protection: Connect to your VPS via SSH using a terminal or SSH client. Once logged in, execute the following command and select Master server when it asks for an option:
wget https://files.voduy.com/vDDoS-Proxy-Protection/latest.sh ; chmod 700 latest.sh ; bash latest.sh
Step 4: Change openlitespeed Default IP
By default aaPanel uses OpenLiteSpeed running on port 80, 443. We can reconfigure these Webservers to listen on another port so that vDDoS can proxy on them. and aaPanel have this config file inside below folders
/www/server/panel/vhost/openlitespeed/listen/
You need to go to files menu in your aaPanel dashboard to access and edit the file 80.conf and 443.conf and chage the default address to 127.0.0.1:80 in 80.conf
listener Default80{
address 127.0.0.1:80
secure 0
mapmorningbharat.com morningbharat.com
mapthephotonnews.com thephotonnews.com
mapcotlasweb.in cotlasweb.in
mapcotlas.net cotlas.net
mapcloud-1.cotlas.net cloud-1.cotlas.net
map default *
}
listener SSL443 {
map thephotonnews.com thephotonnews.com
map thephotonnews.com thephotonnews.com
map cloud-1.cotlas.net cloud-1.cotlas.net
map cloud-1.cotlas.net cloud-1.cotlas.net
map cloud-1.cotlas.net cloud-1.cotlas.net
address 127.0.0.1:443
secure 1
keyFile /www/server/panel/vhost/cert/cloud-1.cotlas.net/privkey.pem
certFile /www/server/panel/vhost/cert/cloud-1.cotlas.net/fullchain.pem
certChain 1
sslProtocol 24
ciphers EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH:ECDHE-RSA-AES128-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA128:DHE-RSA-AES128-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-GCM-SHA128:ECDHE-RSA-AES128-SHA384:ECDHE-RSA-AES128-SHA128:ECDHE-RSA-AES128-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES128-SHA128:DHE-RSA-AES128-SHA128:DHE-RSA-AES128-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES128-GCM-SHA384:AES128-GCM-SHA128:AES128-SHA128:AES128-SHA128:AES128-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!RC4
enableECDHE 1
renegProtection 1
sslSessionCache 1
enableSpdy 15
enableStapling 1
ocspRespMaxAge 86400
}Save both the file and go to aaPanel app store and restart openlitespeed server from there, so that configuration can start working.
Step 5: Config vDDoS Proxy Protection
To configure vDDos Protection in your server now you need to change edit the main configuration file inside /vddos/conf.d/website.conf. Just login to your vps using ssh and run below command to edit the file
nano /vddos/conf.d/website.conf
For example if your vps server ip is 1.2.3.4. then you need to edit the config file as this
# Website Listen Backend Cache Security SSL-Prikey SSL-CRTkey
default http://1.2.3.4:80 http://127.0.0.1:80 no no no no
default https://1.2.3.4:443 https://127.0.0.1:443 no no /vddos/ssl/your-domain.com.pri /vddos/ssl/your-domain.com.crt
When I edited this file the content was already there I just changed the ip and port for listen ip backend ip inside this folder according to my server ip. Now restart the vDDoS server after you have configured.
Restart vDDoS service after you have configured:
/usr/bin/vddos restart
Step 6: Config vDDoS Auto Add
vDDoS Auto Add is a addon support for vDDoS Proxy Protection which adds your websites automatically in your vDDOS website.cof file to Monitor Domains/Aliasdomains/Subdomains in Panel Hosting, Web Server, List Domain, Virtual Host. You need to edit this file using ssh command line:
nano /vddos/auto-add/setting.conf
# Default Setting for vddos-add command:
SSL auto
DNS_sleep 66
DNS_alias_mode no
Cache no
Security no
HTTP_Listen http://1.2.3.4:80
HTTPS_Listen https://1.2.3.4:443
HTTP_Backend http://127.0.0.1:80
HTTPS_Backend https://127.0.0.1:443
Set Crontab:
echo '*/15 * * * * root /usr/bin/vddos-autoadd webserver apache' >> /etc/crontab
Step 7: Configure vDDoS Auto Switch
In next step you need to configure the auto switch method of vDDoS Proxy Protection which automatically identifies overloaded websites and changes their Security Mode. you need to edit this file in ssh according to your requirement. You can get more detail about it here vDDoS
nano /vddos/auto-switch/setting.conf
This is a default file configuration.
# This is the default configuration for "sensor-switch.sh" and "vddos-autoswitch.sh"
hostname="vDDoS Master" #(Name this server, it will show up in Email notifications)
vddos_master_slave_mode="no" #(Turn on "yes" if your system has slave servers, want to sync affter switch like master)
backend_url_check="no" #(Put the URL of the backend. Ex: https://1.1.1.1:8443/ (make sure Backend status response is "200"))
send_notifications="no" #(Turn on "yes" if you want receive notification)
smtp_server="smtps://smtp.gmail.com" #(SMTP Server)
smtp_username="[email protected]" #(Your Mail)
smtp_password="xxxxxxxxxxxxx" #(Get your Apps password for Gmail from https://security.google.com/settings/security/apppasswords)
send_notifications_to="[email protected]" #(Your Email Address will receive notification)
maximum_allowable_delay_for_backend=2 #(Means: If Backend (status response "200") is slower than 2s, vDDoS will enable challenge mode)
maximum_allowable_delay_for_website=2 #(Means: If Website (status response "200") is slower than 2s, vDDoS will enable challenge mode)
default_switch_mode_not_attack="no" #(Default Mode vDDoS use when it's not under attacked)
default_switch_mode_under_attack="high" #(Default Mode vDDoS use when it's under attack)
default_waiting_time_to_release="60" #(For example 60 minutes, release time from challenge)
Crontab vDDoS Auto Switch:
echo '*/5 * * * * root /usr/bin/vddos-autoswitch checkalldomain high' >> /etc/crontab
echo '0 */3 * * * root /usr/bin/vddos-switch allsite no && /usr/bin/vddos reload' >> /etc/crontab
echo '* * * * * root /usr/bin/vddos-sensor' >> /etc/crontab
Problems Faced during this process:
In step 6 above we have configure cron job to run which will add the domain from our panel automaticaly to the vDDoS website.conf file but I dont know whether cron job was running or not because my website was not working, And I tried to add my website in website.conf file by editing it in my ssh terminal nano /vddos/conf.d/website.conf
But when i ran the command to restart the vDDoS server using this command /usr/bin/vddos restart. It was giving me error in website.conf file on line where I have added my website example.com. I tried many times but it was not working and it was also not adding my site in the list automaticaly.
So i decided to manually add cron in aaPanel manually. You can do that by adding cron and adding a this task and executing it manually.
/usr/bin/vddos-autoadd domain example.com
After this my website started showing again, but ssl was not working. because inside the website.conf file of vDDoS it has added a wrong ssl file location. I dont know how to configure the auto add settings file to add correct ssl file location. So I need to to find the correct ssl file location and change it into the website.conf file. You can do so by going to
/usr/bin/vddos-autoadd domain example.com
My website configuration was already added when I executed the cron. aaPanel save the ssl files in /www/server/panel/vhost/cert/, you can find your ssl file location in File manager But first you need to add ssl to your website. And edit the /vddos/conf.d/website.conf file with correct private key and certificate. see example below.
www.example.com http://38.242.153.187:80 http://127.0.0.1:80 no no no no
www.example.com https://38.242.153.187:443 https://127.0.0.1:443 no no //www/server/panel/vhost/cert/example.com/privkey.pem /www/server/panel/vhost/cert/example.com/fullchain.pem
example.com http://38.242.153.187:80 http://127.0.0.1:80 no no no no
example.com https://38.242.153.187:443 https://127.0.0.1:443 no no /www/server/panel/vhost/cert/example.com/privkey.pem /www/server/panel/vhost/cert/example.com/fullchain.pem
And when I accessed my website, this time ssl was working properly. So this was the process to configure your aaPanel vps server with vDDoS Proxy protection. So this is how to configure AntiDDoS Protection on aaPanel with vDDoS Proxy Protection for openlitespeed as backend. If you want to configure it with apache or nginx server you can follow this article here.
https://groups.google.com/g/voduydotcom/c/EU3ALgktgRU?pli=1
Official documentation
https://vddos.voduy.com/
If you want to configure vDDos protection on cyberpanel, you can follow this article here.
https://community.cyberpanel.net/t/antiddos-for-cyberpanel-with-vddos-proxy-protection/34093